Steps for the Multi-server Architecture Deployment
Steps to Install K3s on the SureMDM Server:
The SureMDM server on which the system admin first installs K3s becomes the Master Node, and the other SureMDM servers become Agent/Worker Nodes.
Follow the below steps to Install K3s on the SureMDM Server:
1. Run the below command to install K3s on a Master Node:
curl -sfL https://get.k3s.io | K3S_KUBECONFIG_MODE="644" INSTALL_K3S_EXEC="server --disable=traefik" sh -
2. Run the following command to restrict kubectl access only to sudo users:
sudo chmod 600 /etc/rancher/k3s/k3s.yaml
3. Run the below command to get a token from Master Node.
sudo cat /var//lib/rancher/k3s/server/node-token
4. Run the following command on other agent nodes:
curl -sfL https://get.k3s.io | K3S_NODE_NAME=$HOSTNAME K3S_URL=https://<IP of server>:6443 K3S_TOKEN=< Token > sh -
- K3S_URL - Enter the IP of Master Node.
- K3S_TOKEN - Enter the token obtained from the previous command.
Example of token format:
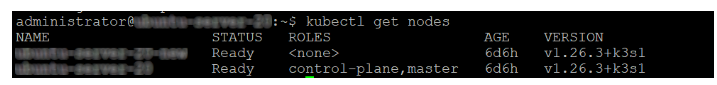
5. Once done, you can check the status of the all nodes using the following command:
kubectl get nodes
The following output can be seen:
6. Download and import the offline images for SureMDM Deployment:\ The system admin should download the offline images (Please refer to General Requirements for details) using the link provided by the 42Gears Support team and import them into the SureMDM Server.
Follow the below steps to import the images:
a. Navigate to the directory where the images are located and execute the following command:
sudo k3s ctr images import image_name
Replace image_name in the above command with the actual name of the image file.
b. Similarly, import each image individually on all the Master and Agent nodes.
The system admin can run the below command to view the list of all imported images:\ sudo k3s ctr images ls
Follow the below steps to setup SureMDM On-premise:
Open the Terminal on the SureMDM Server and navigate to the k8sopinstaller directory (where the SureMDM installer is downloaded and extracted).
To begin, execute the following command:
sudo bash super_install.sh
- After running the above command User will see the following output:
Thank you for selecting SureMDM OnPremise for your deployment.
Could you kindly specify the number of devices you plan to manage within your setup: <Enter the number>
You are configuring for <number> devices. Do you wish to continue? Yes[y] or No[n]:
Thank you for your input. Please find the checklist below:
The user should provide the number of devices planned to manage within the setup
Press ‘y’ to continue with the same device count, or press ‘n ‘ to change the device count.
- Next, provide the values for SQL DB Server setup to setup:
SQL server setup for SureMDM:
Please enter the SQL Server Credentials and Connection String.
Please enter SQL Server Path:
Please enter SQL Server Username:
Please enter SQL Server Password:
Provide the SQL DB Server path using the following format: 192.168.x.xx (Private IP Address of the machine).
- Provide the values for MongoDB Server setup:
MongoDB server setup for SureMDM:
Please enter MongoDB Server connection string(ex : mongodb://192.168.x.xx:27017):
Provide the MongoDB server Connection String using the following format (always use the private IP of the machine): mongodb://192.168.x.xx:27017
- Next, choose the Storage Configuration setup from the following option:
Storage setup for SureMDM:
1. Configure AWS S3 bucket for Storage.
2. Configure MinIO bucket for Storage.
If the system admin selects option 1, then the following AWS S3 bucket details must be provided:
AWS S3 Bucket Name:
AWS S3 Icon Bucket Name:
AWS S3 Access Key:
AWS S3 Secret Key:
AWS S3 Region:
AWS S3 Report Bucket Name:
AWS S3 Report Access Key:
AWS S3 Report Secret Key:
AWS S3 Report Region:
If the system admin selects option 2, then the following MinIO bucket details must be provided:
Minio Bucket Name:
Minio Icon Bucket Name:
Minio Access Key:
Minio Secret Key:
Minio Region:
Minio Service URL: https://xxxxxx.abc.com
Minio Report Bucket Name:
The system admins are recommended to have two S3 buckets (one bucket will be used for jobs and reports, while the other will be used for application icons).
Messaging system configuration will be done.
The next step is to enter the mapped DNS without the HTTPS protocol:
Please enter your SureMDM Account URL:
- System admins must provide the DNS without the subpath extension (/suremdm).
- If the system admins wish to deploy SureMDM on-premise on a port other than 443, they can specify it, for example: abc.suremdm.com:8447.
- SSL Certificate Configuration:
SSL certificate Configuration:
Please ensure that the SSL Certificate and Private Key available in 'appdata/certs' folder.
Enter the file name of the SSL Certificate:
(Example: file_name.extension):
Enter the file name of the Private Key associated with the Certificate:
(Example: file_name.extension):
- Select the FCM configuration based on the requirements:
FCM configuration:
Do you wish to continue with FCM configuration? Yes[y] or No[n]:
If system admins want to continue with the **FCM configuration**, they can enter "y" by providing the following details; otherwise, they can enter "n".
FCM Project ID:
FCM Server API Key:
FCM Application ID:
FCM Sender ID:
Please enter the name of .json file present in the appdata/pluto directory.(Example:[file_name.json]):
Click here to learn how to generate the FCM key.
- Select the Google API key configuration based on the requirements:
Google Maps configuration:
Do you wish to use Google Maps with the SureMDM setup? Yes[y] or No[n]:
If the system admins want to continue with the Google API key configuration, they can enter "y" by providing the Google API key; otherwise, they can enter "n".
Google API Key:
The customer should purchase the Google API key. Otherwise, they can use the default OpenStreet maps available in SureMDM.
- Select the iOS and macOS configurations based on the requirements:
Do you wish to continue with iOS and macOS configuration? Yes[y] or No[n]:
If the system admins want to continue with the iOS and macOS configuration, they can enter "y" by providing the DefaultPush certificate password; otherwise, they can enter "n".
Enter Default Push Certificate Password:
- Select the Android Enterprise configuration based on the requirements: Android Enterprise Configuration:
Do you wish to continue with the Android Enterprise configuration? Yes[y] or No[n]:
If the system admins want to continue with the Android Enterprise configuration, they can enter "y" by providing the following details; otherwise, they can enter "n".
Please enter the name of the MSA Account Certificate in the appdata/api/appdata directory.
(Example:[file_name.p12]):
Please enter the name of the ESA Account Certificate in the appdata/api/appdata directory.
(Example:[file_name.p12]):
Please enter MSA Account Email:
Please enter ESA Account Email:
System admin can skip the ESA details based on their requirements.
- Select the Mail configuration based on their requirements:
Mail server configuration:
Do you wish to continue with Mail server configuration? Yes[y] or No[n]:
If system admins want to continue with the Mail configuration, they can enter "y" by providing the following details; otherwise, they can enter "n".
Enter Mail server:
Enter Mail user:
Enter Mail password:
Enter Mail Server Backup:
Press Enter to skip Mail Server Backup details based on their requirement.
- Select the Windows Push Notification Configuration based on the requirements:
Windows Push notification configuration:
Do you wish to continue with the Windows Push Notification Configuration? Yes[y] or No[n]:
If the system admins want to continue with the Windows Push Notification configuration, they can enter "y" by providing the following details; otherwise, they can enter "n".
Enter Package Family Name:
Enter SID:
Enter Client Secret:
- Select the MQTT Gateway (Things Enrollment) configuration based on the requirements:
MQTT gateway(IoT/Things enrollment) configuration:
Do you wish to continue with MQTT gateway configuration? Yes[y] or No[n]:
If the system admins want to continue with the MQTT Gateway (Things enrollment) configuration, they can enter "y"; otherwise, they can enter "n".
Port 1883 should be allowed. Click here to learn how to configure Things QR enrollment (CamLock and CamLock Sentry).
- Select the SureMDM Hub configuration based on the requirements:
SureMDM Hub configuration:
Do you wish to continue with SureMDM Hub configuration? Yes[y] or No[n]:
If the system admins want to continue with the SureMDM Hub configuration, they can enter "y" by providing the following details; otherwise, the system admin can enter "n".
Enter SureMDM Hub Email-ID:
Enter SureMDM Hub Company Name:
Note: The username "Administrator" will be the default admin user for SureMDM Hub.
- The default admin user for SureMDM Hub will be username with Administrator.
- For a new setup of SureMDM Hub, run the following queries once the deployment is completed:
- a. Click here to get the MongoDB query for SureMDM Hub.
- b. Click here to get the SQL DB query to connect account ID 1 to SureMDM Hub.
- c. Click here to get the SQL DB query for SureMDM Hub.
- d. Click here to get the SQL DB query to assign the license to account ID 1.
- e. Click here to get the MongoDB query for changing deployment from a single tenant to SureMDM Hub and this query needs to be run in suremdmadmindb.
- Once deployment is successful, the system admins can see the following message:
SureMDM Configuration Successful! Please wait for some time and then access SureMDM Web Console.
- The system admins can check the status of the pods by running the command.
kubectl get pods -n suremdm. - Run the following command to obtain the IP address of the machine to which the DNS should be mapped:
sudo kubectl get ingress -n suremdm